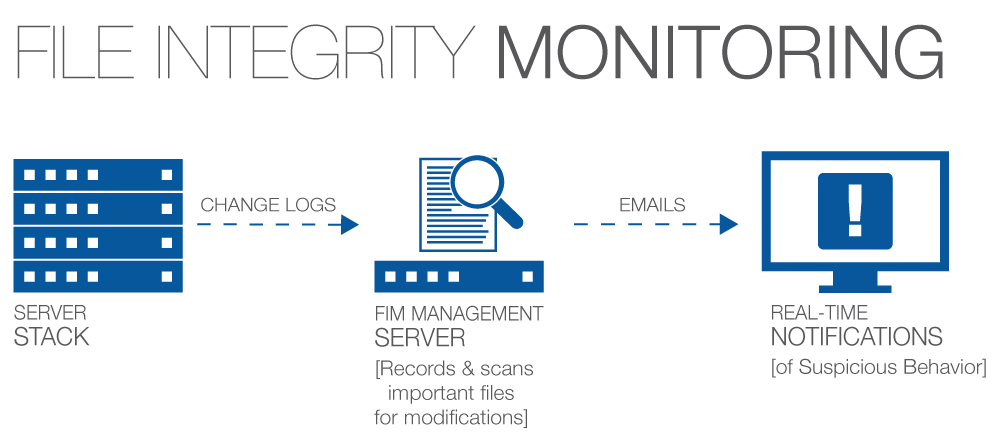
With an increase in the threat of potential data breach by the ever increasing force of hackers, there has been an appreciable increase in the precautionary solutions designed for combating such attacks. When we talk about compliance, the first thing that strikes our mind is file integrity monitoring. However, compliance is not the only parameter in which it can prove to be crucial. There are many other goals and objectives of a particular security program, which can be enhanced with the help of file integrity monitoring. In this article, let us discuss about these other factors in a detailed manner.
Objectives Relevant to File Integrity Monitoring
In this section, we will get an insight of some parameters apart from compliance, wherein file integrity monitoring plays a significant role:
1. Secured Network: Having a secured network does not imply the deployment of firewalls and server security only. Whilst most of the security breaches are a result of known vulnerabilities, using firewall and server security is not enough. It is necessary to keep in mind the components like servers, systems, mobile devices, etc. The file integrity monitoring systems which are agent-based allows the network admins to monitor the integrity of the files that are stored in all the connected devices.
2. Prevention of Unauthorized Access: Unauthorized access of an organization’s network poses grave dangers and can cause damage to the organizations reputation as well as decrease its market value. The unauthorized access can take many forms among st which the common is sharing of devices in an unauthorized manner and hacking of business accounts, which ultimately lead to data theft. File integrity monitoring helps in the process of auditing in case the access control methodologies somehow fail. Since the negative changes will be identified in real-time, the admin can take preventive measures to safeguard the network.
3. Vulnerability Scanning: This is yet another aspect which can be taken care of by file integrity monitoring software. The software can enable the administrator to discover the risks that can be analyzed within the vulnerability management framework. Complexities of networks, threat vector, and other threats can be handled with a perfect file integrity monitoring tool in the organization.
4. Integrity of Network Assets: Maintaining the integrity of all the data assets, it takes more than just education and policies. This is where file integrity monitoring comes into scenario and allows the security program in the network to continue to grow and continue to work. The effective monitoring systems integrate seamlessly into your network and change as per the changes in the network.
5. Immediate Reporting of Security Flaws: No training in this world can ensure that no employee will fall in the traps of phishing and other security breaches. File integrity monitoring cannot be of any help in improving the poor culture of security knowledge and ethics and can never change or train the employees to not security mistakes. However, it can be of great support in minimizing the after effects of the mistakes done from the employees.
File Integrity monitoring software is an invaluable asset of an organization, ensuring perfect security of your network.